TROOPERS is a well-established, international IT security conference with more than 3,500 attendees in ten years and speakers from 25+ countries. This year was the 15th time the conference took place in Heidelberg, Germany. The attendees from all over the world were able to enjoy a wide variety of technical talks divided into three categories: Attack & Research, Defense & Management, and Active Directory & Azure Security.
Attending this conference is an excellent opportunity for our Vulnerability Researchers to meet with the IT security community, keep up with the latest research trends and share their own knowledge by presenting a talk. Especially the wide variety of covered technologies and their related security challenges provide a great way to get a broader perspective and gain valuable insights, which are not only relevant to a specific technology.
Venue and Events
The conference took place in the halle02 in Heidelberg for the second time. This venue, usually used to host music events, is a converted warehouse and provides a lively but cozy atmosphere, which is a perfect fit for a technical conference like this:

https://twitter.com/WEareTROOPERS/status/1674345822022975488
The actual TROOPERS conference was preceded by two days of on-site training offering different topics such as Malware Analysis, Hacking Enterprises, and Incident Analysis. The conference itself was enriched by various events like a shared dinner with live music, a CTF-like PacketWars competition, and a roundtable discussion covering current IT security topics such as Cloud Security. Furthermore, there were different charity events like a 10k run and an auction to raise money for a good cause.
Talks
The three parallel tracks allowed a wide variety of topics and a total amount of 36 talks throughout the two days of the TROOPERS conference:
The keynote provided by Mikko Hypponen outlined the ways technology has changed our lives. This includes controversies such as organized crime carried out by ransomware groups, which offer 24/7 customer support to ensure their good reputation. Another topic that we cannot avoid when talking about today’s technology is, of course, AI. What will happen if we feed a code-writing AI with its own code over and over again to improve itself? Will we still be able to understand and control this creation?
The talk Cat & Mouse - Or Chess? by Fabian Mosch explained how the latest Antivirus and EDR solutions identify malware by using userland hooks and which different techniques exist to bypass these. By adopting a recent AMSI bypass method, Fabian implemented a new way to also avoid EDR detection by suspending a process and preventing the EDR DLL from being loaded.
Alexander Heinrich and Jiska Classen presented their impressive research about Ultra Wideband technology in the talk Attacking Ultra Wideband: Security Analysis of UWB Applications in Smartphones. The outlined attacks use different approaches to shorten the distance measured by Ultra Wideband devices. Since this technology is used to open modern cars, this potentially allows criminals to carry out relay attacks to steal these cars.
The talk Testing and Fuzzing the Kubernetes Admission Configuration by Benjamin Koltermann and Maximilian Rademacher nicely explained how Kubernetes Admission Controllers work and what they are used for. Additionally, Benjamin and Maximilian presented a new tool to fuzz and test the configuration, which they demonstrated during a live demo.
Monitoring Solutions: Attacking IT Infrastructure at its Core
On the second conference day, our Vulnerability Researcher Stefan presented the talk Monitoring Solutions: Attacking IT Infrastructure at its Core:
https://twitter.com/spoookyM/status/1674393734836789248
A recording of the talk can be found here: YouTube - TROOPERS23: Monitoring Solutions: Attacking IT Infrastructure at its Core.
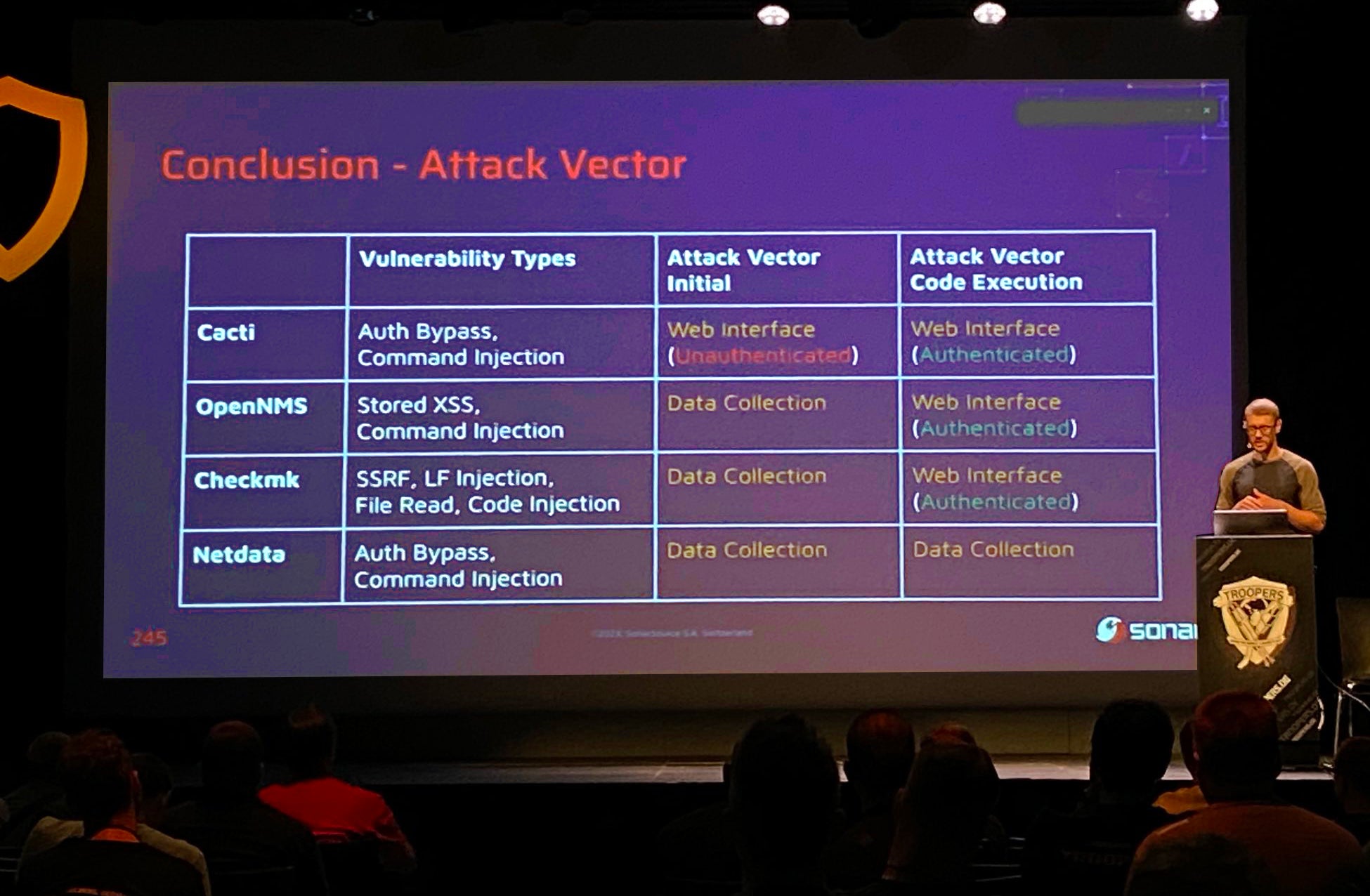
The talk outlined the necessity and importance of monitoring solutions and their value for attackers. Based on the technical architecture of common monitoring solutions, the corresponding attack surface is derived. After this, the talk deep-dives into four case studies covering Cacti, OpenNMS, Checkmk, and Netdata. For all these case studies, the code vulnerabilities we discovered resulted in a full Remote Code Execution chain showcased with individual exploitation demos during the talk. The conclusion summarized the common patterns of all code vulnerabilities, explained how these can be prevented, and what security researchers can learn from this. This demonstrates how important Clean Code is to prevent such attacks.
Thank you to everyone attending the talk and to the organizers for having us!
For everybody interested in the details about the related vulnerability, we recommend reading the following blog posts (articles on OpenNMS and Netdata will be published soon, too):
- Cacti: Unauthenticated Remote Code Execution
- Checkmk: Remote Code Execution by Chaining Multiple Bugs (part 2, part 3)
- It’s a (SNMP) Trap: Gaining Code Execution on LibreNMS (not covered in the talk)
There were a lot of great talks throughout the conference. You can check out the complete list here.
Conclusion
The TROOPERS 2023 conference was awesome. The versatile venue, combined with the kindness and openness of all attending people, created a very enjoyable atmosphere. The different events alongside the high-quality talks additionally enrichened the overall experience. We would be very happy to be part of this great event again next year!

https://twitter.com/spoookyM/status/1674440874380472322
Until then, we are looking forward to the following upcoming conferences, where we will present parts of our research:
- WeAreDevelopers Word Congress, July 27-28 in Berlin
- DEFCON, August 10-13 in Las Vegas
- Hexacon, October 13-14 in Paris
And more to come soon!

