On October 14-15, members of our Vulnerability Research and AppSec teams traveled across Europe to attend Hexacon 2022 in Paris at the Maison de la Mutualité.

This is the first edition of this event organized by the French security firm Synacktiv: the goal was to build a community-oriented event around offensive security for industry professionals. With about 500 attendees, Hexacon is the first large-scale French event with such promise.
Talks
Aside from the community, this event's other huge benefit is accessing world-class content. It helps our teams to keep up-to-date with the latest research and drive our innovative technology in the right direction. Overall, we were very impressed with the variety of topics covered during the conference, their high level of technicity, and we did learn a lot. You can find a list of personal favorites below.
Hacking the Cloud with SAML by Felix Wilhelm was an exciting piece of research. Felix discovered multiple security bugs in SAML implementations. SAML happens mainly in the context of Single-Sign-On (SSO) solutions, critical components of any modern organization. One of his findings is in the JIT compiler of the Xalan-J XSLT processor, part of the Java virtual machine. Who could have expected to find such a compiler here? You can find the slides here.
Airbus Security Lab presented their methodology that yielded about 30 CVEs in the enterprise backup solution called Veritas NetBackup, which suffers from 20 years of technical debt. The vulnerabilities discovered are part of the most frequent ones introduced by developers, the kind of ones you would find in the OWASP Top 10. Injections and XXEs, among others, are still very much alive, even in enterprise software! You can find the slides here.
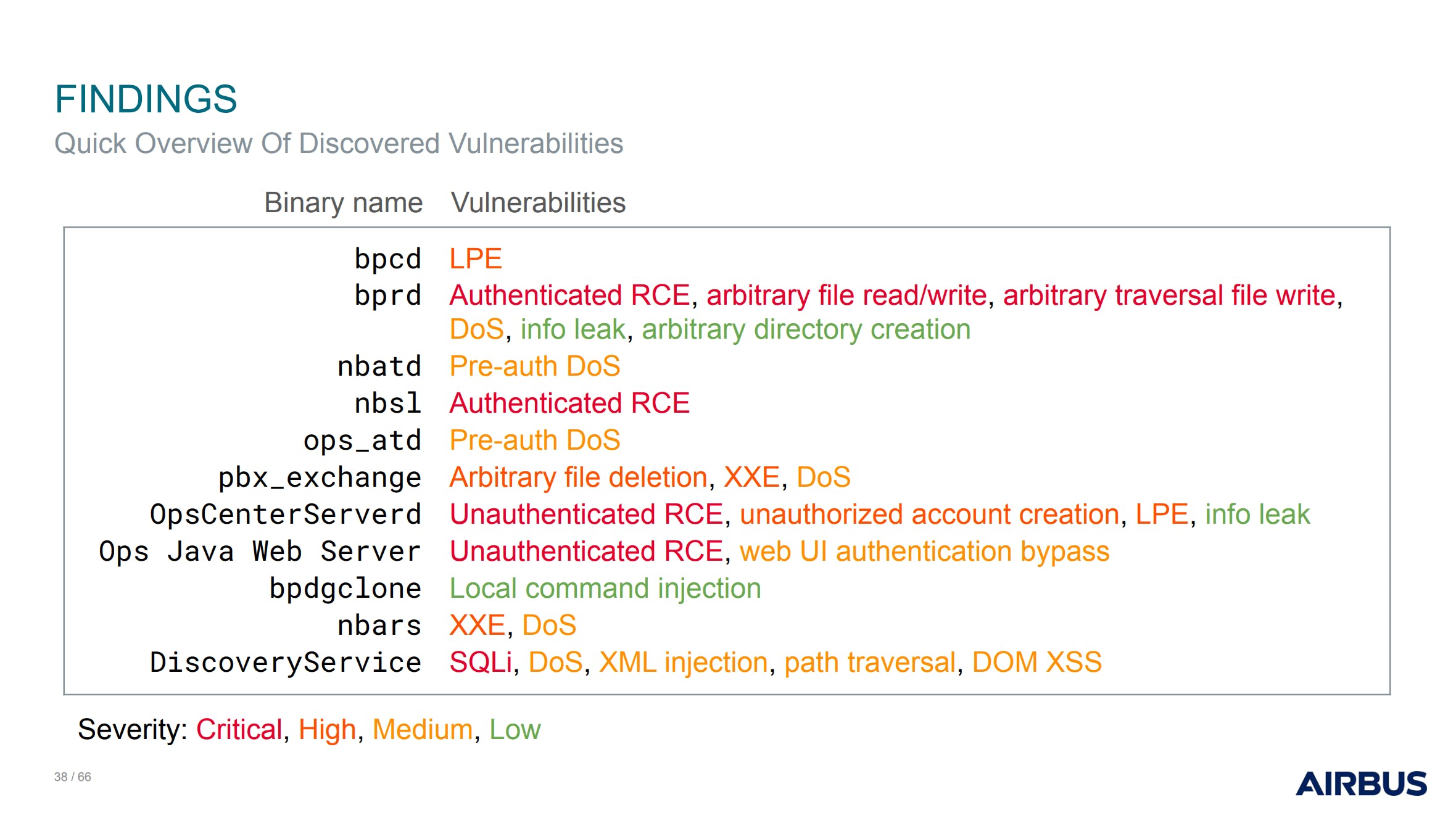
Slide from Airbus' talk showing their various findings.
At the end of the first day, David Bérard and Vincent Dehors from Synacktiv presented a remote vulnerability in the wi-fi stack of the Tesla Model 3. With what appeared to be a weak primitive that allowed them to swap specific bytes over the air with a vulnerability in the connectivity service, they managed to execute arbitrary code on the infotainment component and open the trunk of a real car, live during the competition Pwn2Own! You can find the slides here.
We also attended multiple talks related to the security of iOS devices. A general takeaway is that Apple made the cost of real-world exploits rise to make it economically uncertain for offensive security companies. Among other processes that also involved producing safer code and reducing the overall attack surface of the most exposed services, Apple introduced an evergrowing list of mitigations, both on hardware and software. It is also much harder for individuals to engage in any new research as the initial "cost of entry" increases.
Finally, Andy Nguyen from Google demonstrated how Blu-ray supports the standard BD-J, allowing the execution of Java code directly from the disk—it's a documented feature! Once again, this is a very unexpected attack surface to find in high-end gaming devices. With this initial entry point, he could escape the Java sandbox and exploit a FreeBSD kernel vulnerability to gain full privileges on both the PS4 and PS5 consoles.
We enjoyed many other talks, but they couldn't all fit here; click here for the complete list.
You've got mail! And I'm root on your Zimbra server
On Friday morning, Thomas from our Vulnerability Research team presented You've got mail! And I'm root on your Zimbra server.

Image courtesy of the Hexacon organizers on Twitter.
In this talk, we presented vulnerabilities we identified in the enterprise webmail software Zimbra. First, we described a simple Stored Cross-Site Scripting vulnerability. This bug class is critical in the context of webmails, as attackers could start exfiltrating your address book, emails, and their attachments!
Then, we went deep into a new-line injection in the cache layer, enabling attackers to steal clear-text credentials from active Zimbra users.
Finally, we did a live demonstration of a remote code execution bug in Amavis, a component dedicated to post-process incoming emails, for instance, to check for any known malware or phishing attempts. We based this demonstration on a bug in the archive extraction tool unrar, tracked as CVE-2022-30333.
We believe that presenting the details of these vulnerabilities, several months after their patch, is crucial to the security industry. While Zimbra addressed the root cause of our discoveries, threat actors are still looking closely at Zimbra and successfully engaging in some in-the-wild exploitation campaigns using 0-day bugs. We also provided general recommendations regarding the security design of this product to reduce the overall risk of privilege escalation.
We received positive feedback on the talk and would like to thank the audience for the fruitful discussions that followed!
You can find a written explanation of these vulnerabilities in our blog too, in Zimbra 8.8.15 - Webmail Compromise via Email, Zimbra Email - Stealing Clear-Text Credentials via Memcache injection and Unrar Path Traversal Vulnerability affects Zimbra Mail.
We will update this article with a link to the recorded talk as soon as it becomes available. Meanwhile, you can find our slides here.
Conclusion
Our teams had a blast; we now look forward to attending OffensiveCon in May and Hexacon 2023! We also want to thank everybody involved in this event (organizers, trainers, speakers, audience, etc.).
Sonar believes security issues are best addressed when the code is being developed. Our true Shift Left approach to Clean Code embeds security as an integral part of the development and identifies issues in source code as it’s being written. With our unique Clean as You Code approach, issues are addressed upfront and no new issues end up in the released code. If you haven't discovered the power of the Sonar solution yet, you can learn more here.
If you want to help us bring our static analysis technology to the next level and attend these events with our team, don't hesitate to look at our open security engineering positions: AppSec Researcher, Vulnerability Researcher, Static Analysis Scientist; many more to be found on our careers page!

