DevOps and CI/CD
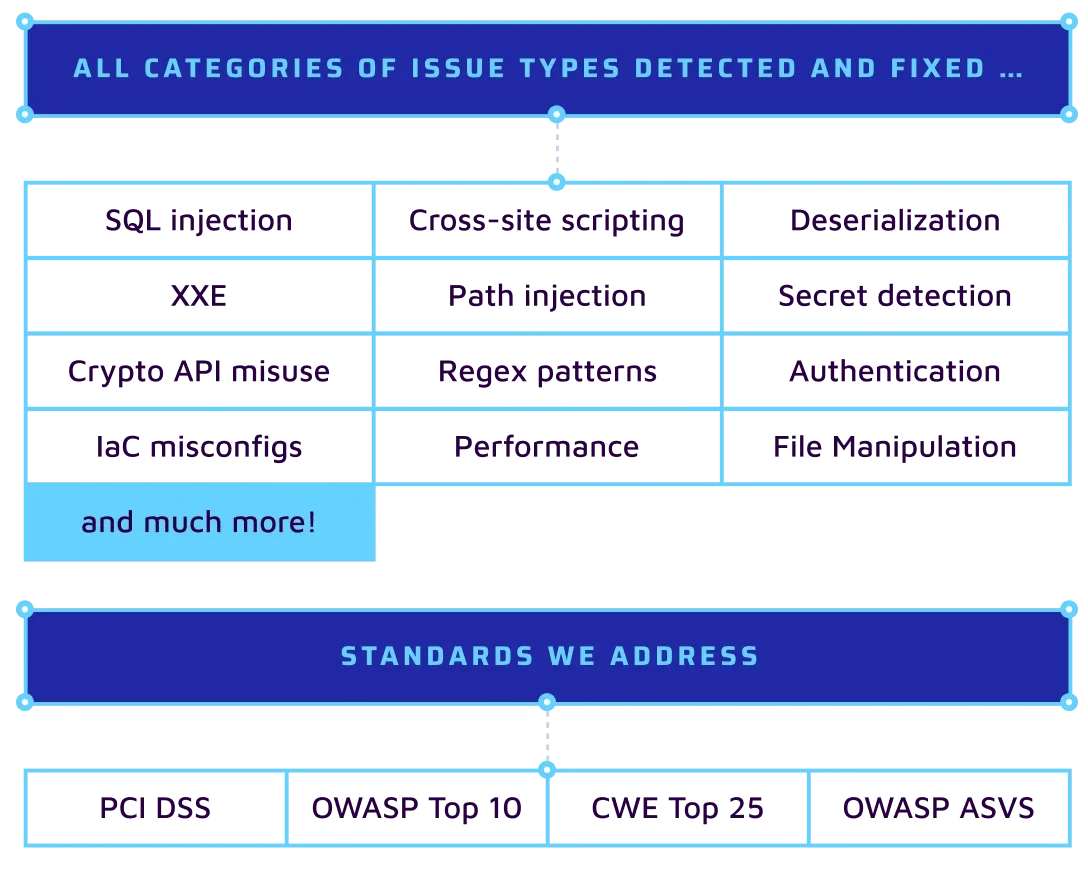
Integrating SAST into the DevOps and CI/CD pipelines empowers organizations to enhance the security posture of their software and ensure that vulnerabilities are identified early in the development lifecycle. Security analysis tools become an integral part of the development process and receive early real-time feedback as they commit code changes. Sonar integrations are supported for popular DevOps and CI/CD Platforms including GitHub, GitLab, Azure Devops, TravisCI, CircleCI, and Bitbucket. Sonar provides native support for the most popular SCMs including Git , Subversion and community support for other popular SCMs such as CVS, Jazz RTC, Mercurial, TFVC.