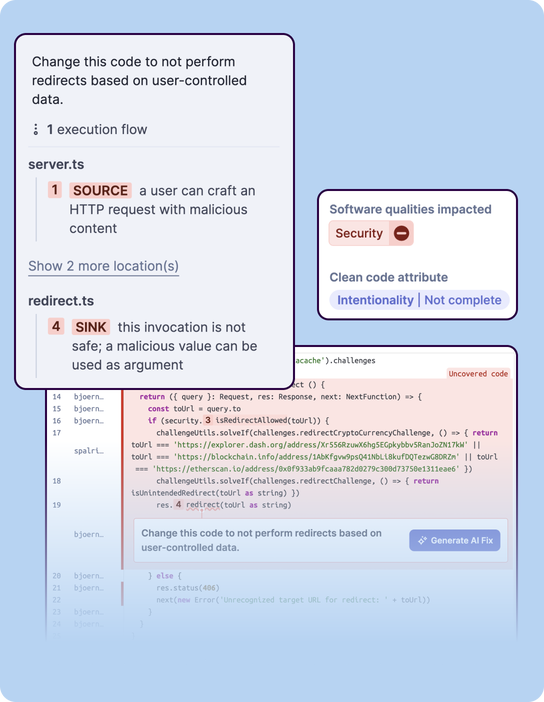
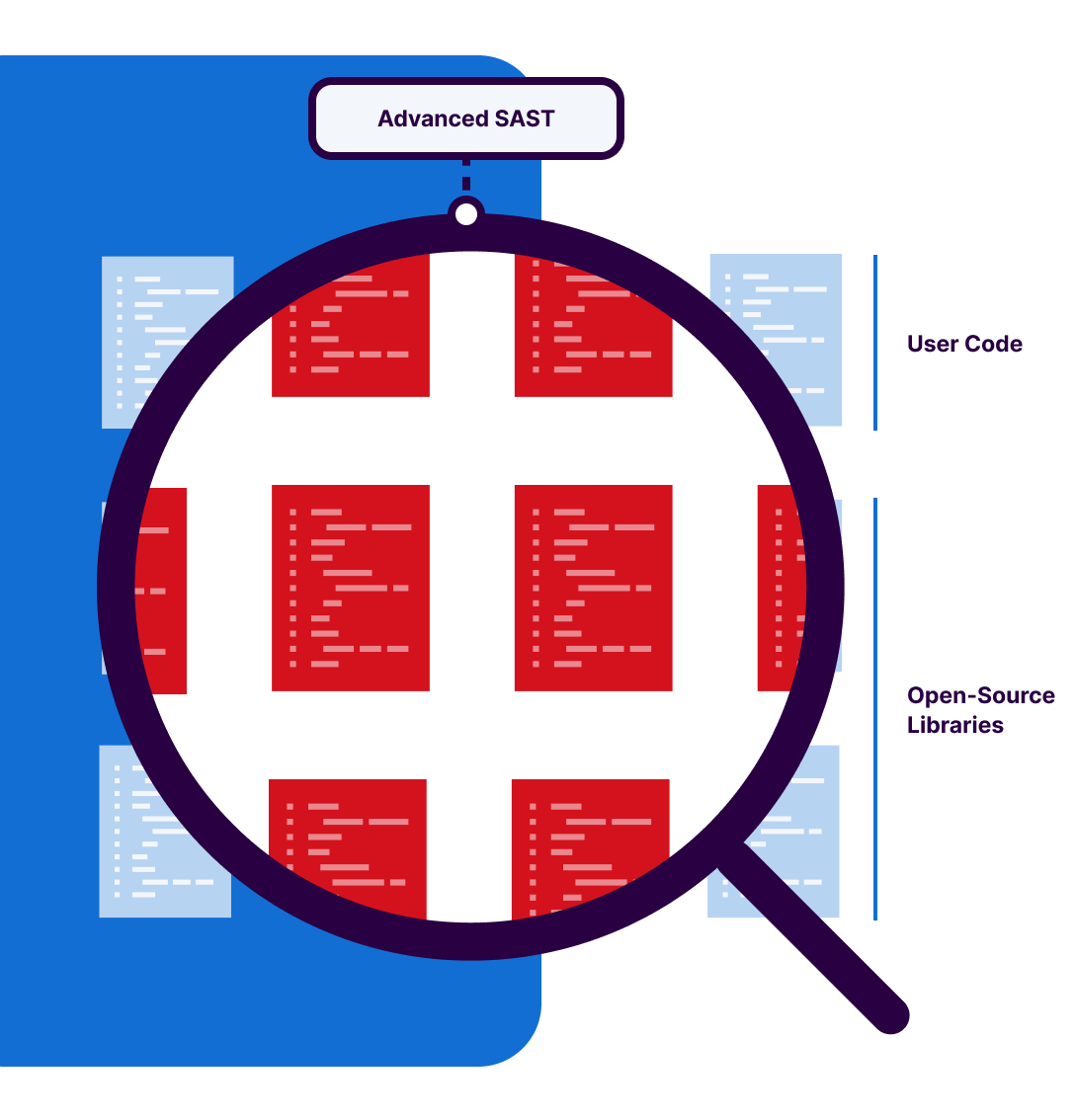
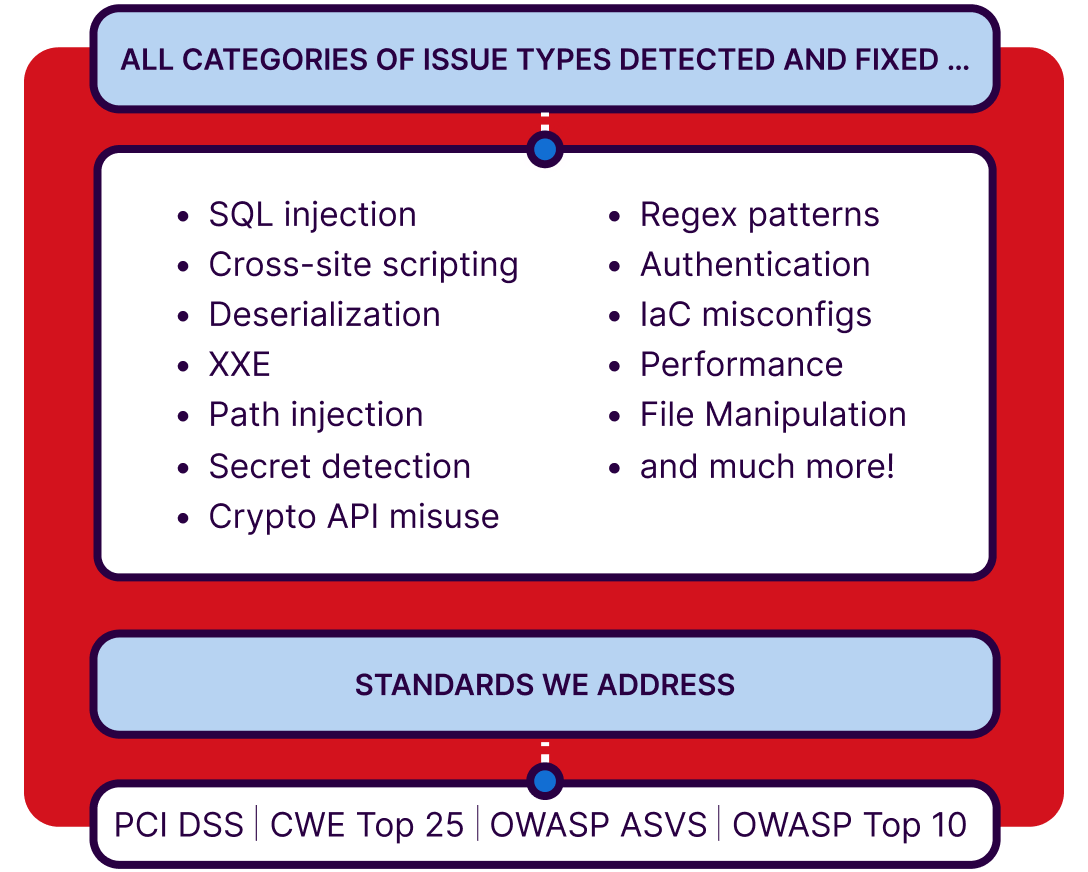
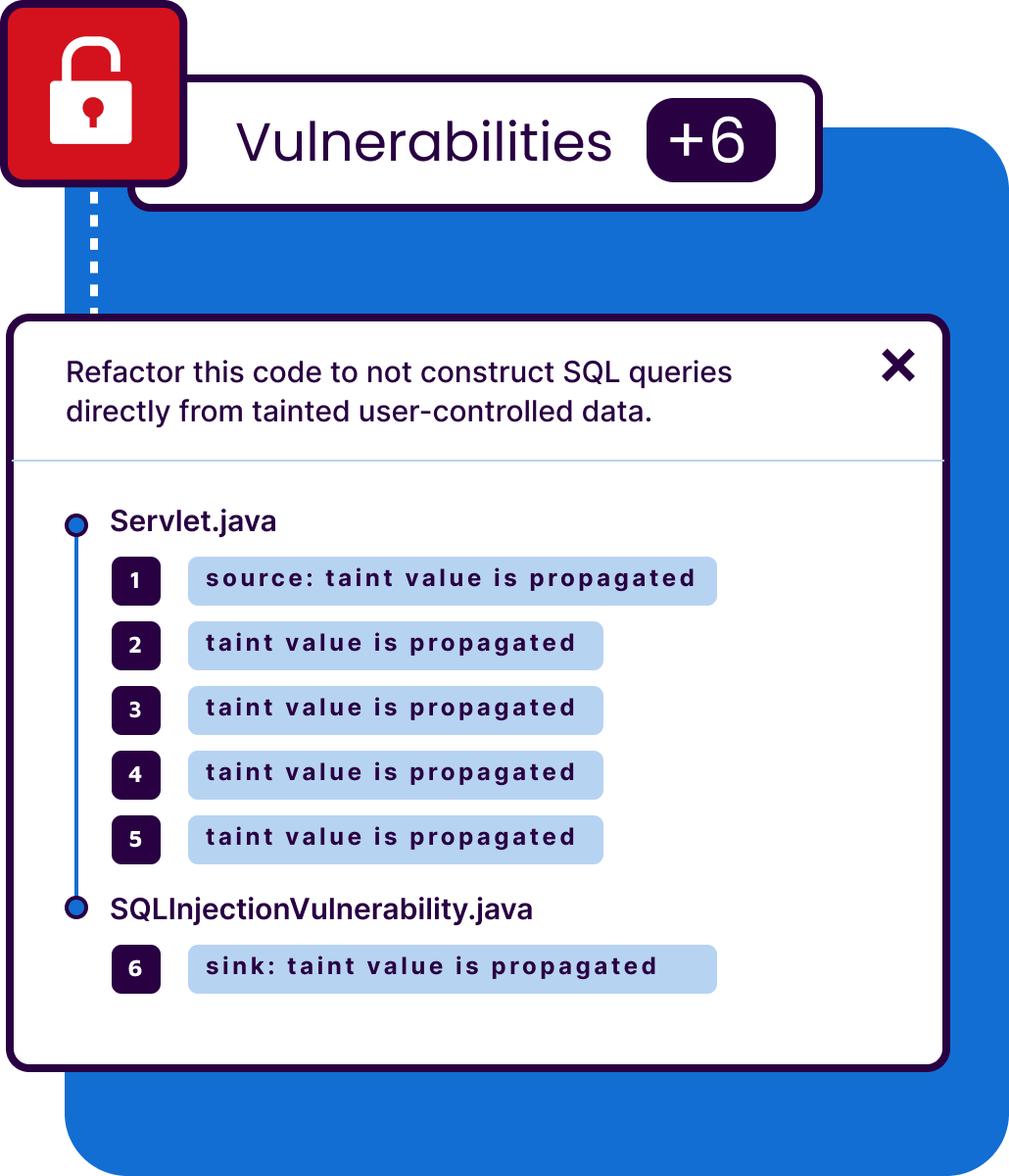
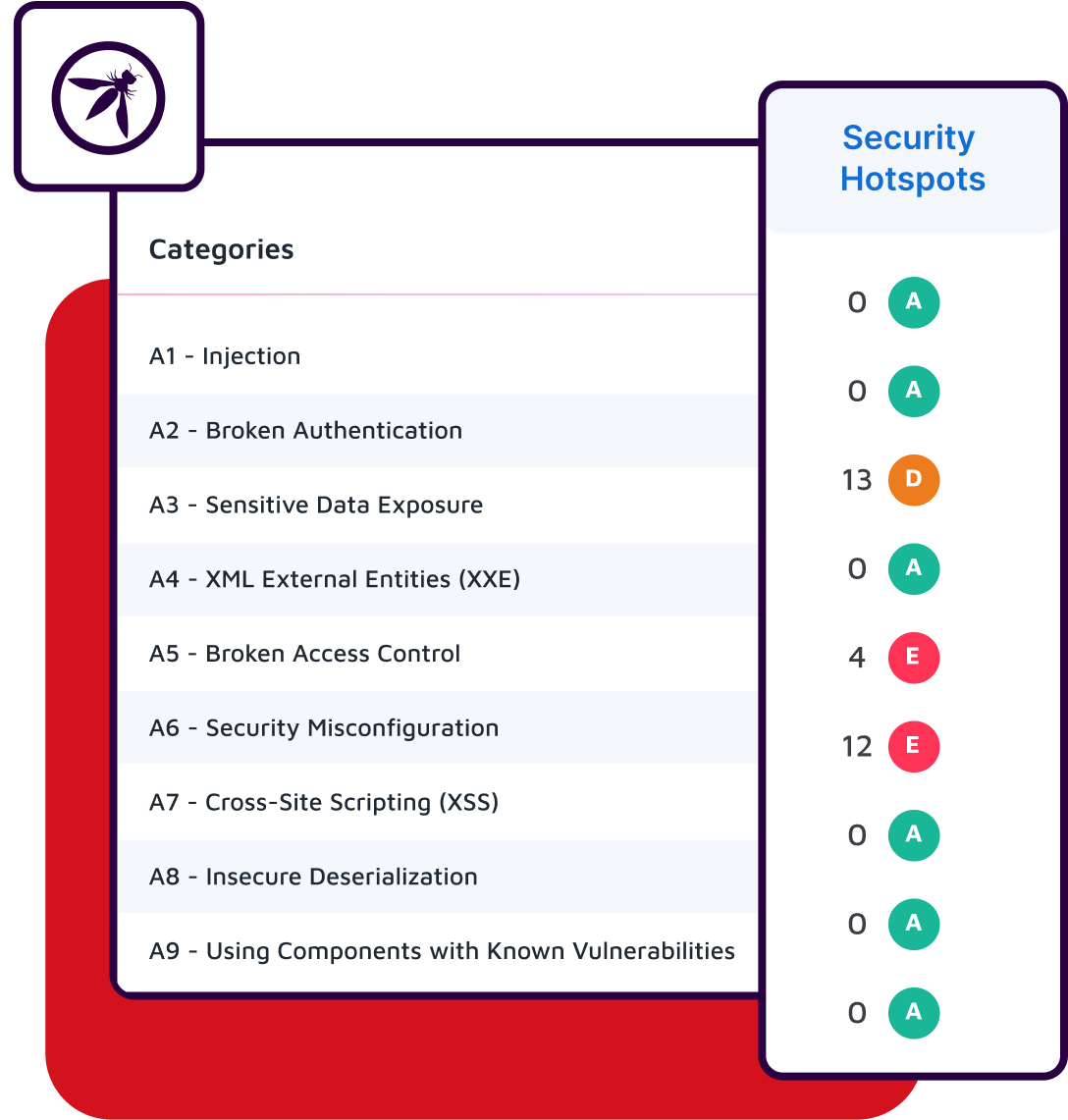
Eliminate blind spots in code interaction
Traditional static analysis cannot look inside a library,leaving a critical blind spot. Advanced SAST overcomes this by extending taint analysis to trace data flow into and out of the third-party libraries. This enables it to uncover deeply hidden, complex vulnerabilities that arise from how your first-party code actually uses the dependencies. As a result, you gain actionable visibility into real application behavior, rather than relying on incomplete or surface-level insights.