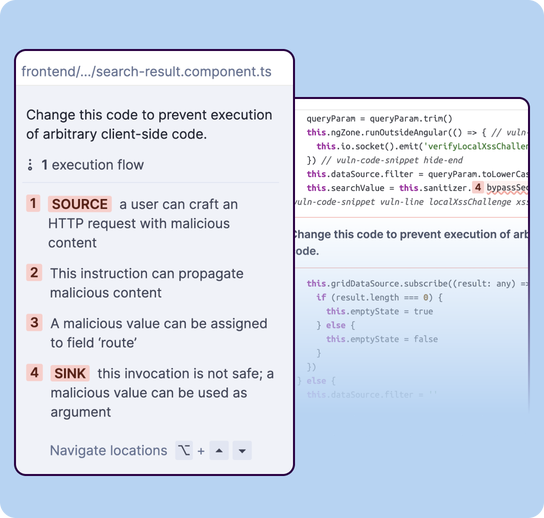
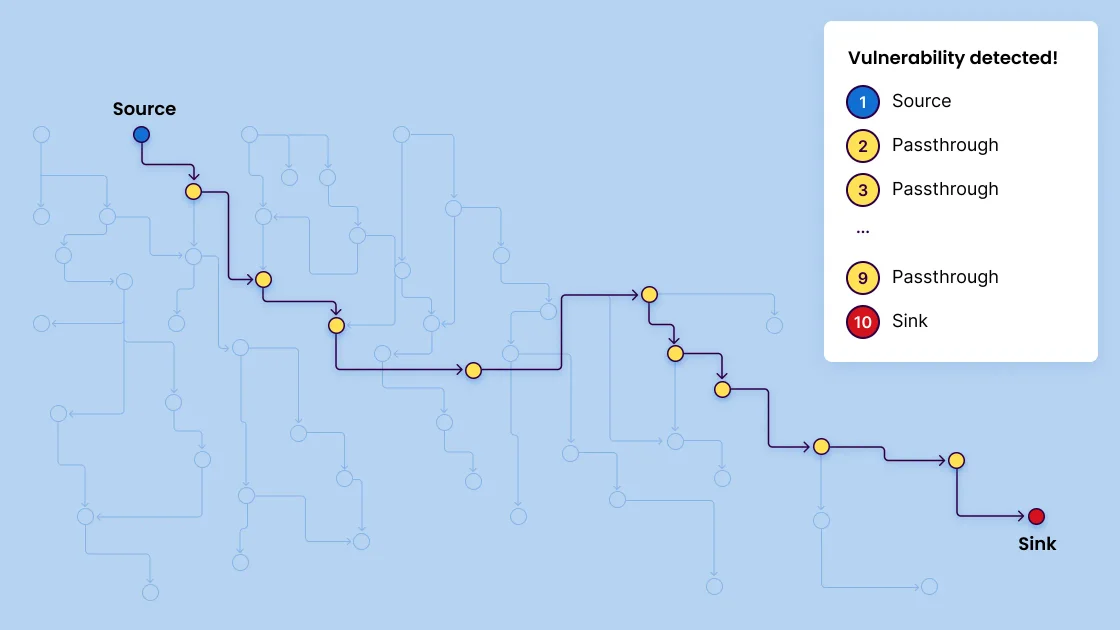
Taint analysis operates by modelling four core elements within the code:
Taint source: The entry point of untrusted data, such as a user HTTP request
// 1) Taint source: untrusted user input
function handleRequest(req) {
const userInput = req.query.username; // sourcePassthrough: A function or process that parses and returns untrusted data, effectively allowing untrusted data to flow through it
// 2) Passthrough: data flows through code
let name = userInput;Sanitizer/Validator: A function or process that cleanses or validates the data, neutralizing the security risk before the data reaches a sink.
// 3) Sanitizer / validator
function sanitize(str) {
//very simple example: allow only letters and numbers
return str.replace(/[^a-zA-Z0-9]/g, '');
}
name = sanitize(name); // sanitize before usingSensitive sink: A function where untrusted data could cause harm, such as executing a system command, or running a database query.
// 4) Sensitive sink: where misuse could cause trouble
// e.g., inserting into HTML without escaping, or running a command
console.log('Welcome, ${name}!`); // safe if sanitized
// If we skipped sanitize, this could risk injection in other sinksA vulnerability is found when the analysis discovers an uninterrupted path from a source to a sink without passing through an adequate sanitizer or validator.