Start your free trial
Verify all code. Find and fix issues faster with SonarQube.
始めましょうYou didn’t write the bug, but you might be the one fixing it on a Saturday night. This is the reality of modern application development, where a significant portion of your codebase consists of open source components you didn’t author.
While frameworks like Spring Boot accelerate development, they also introduce a complex web of dependencies. A single line in your pom.xml can pull in a library, which pulls in another, creating a hidden chain of code that enters your application. If a vulnerability exists deep in that chain—like a "Trojan horse" hiding inside a trusted package—your entire application is at risk.
Here is how SonarQube Advanced Security helps you identify and neutralize these hidden threats before they reach production.
The invisible threat of transitive dependencies
A common scenario involves adding a trusted library to your project. It works perfectly, but without anyone knowing, it relies on an older, vulnerable version of another library (e.g., a logging utility or web server). You never explicitly added the vulnerable component, but it is now part of your deployable artifact.
This "dependency hell" makes manual tracking nearly impossible. You might rely on a reporting tool that is safe, but if that tool relies on a compromised library, your application inherits the vulnerability.
Actionable visibility with Software Composition Analysis (SCA)
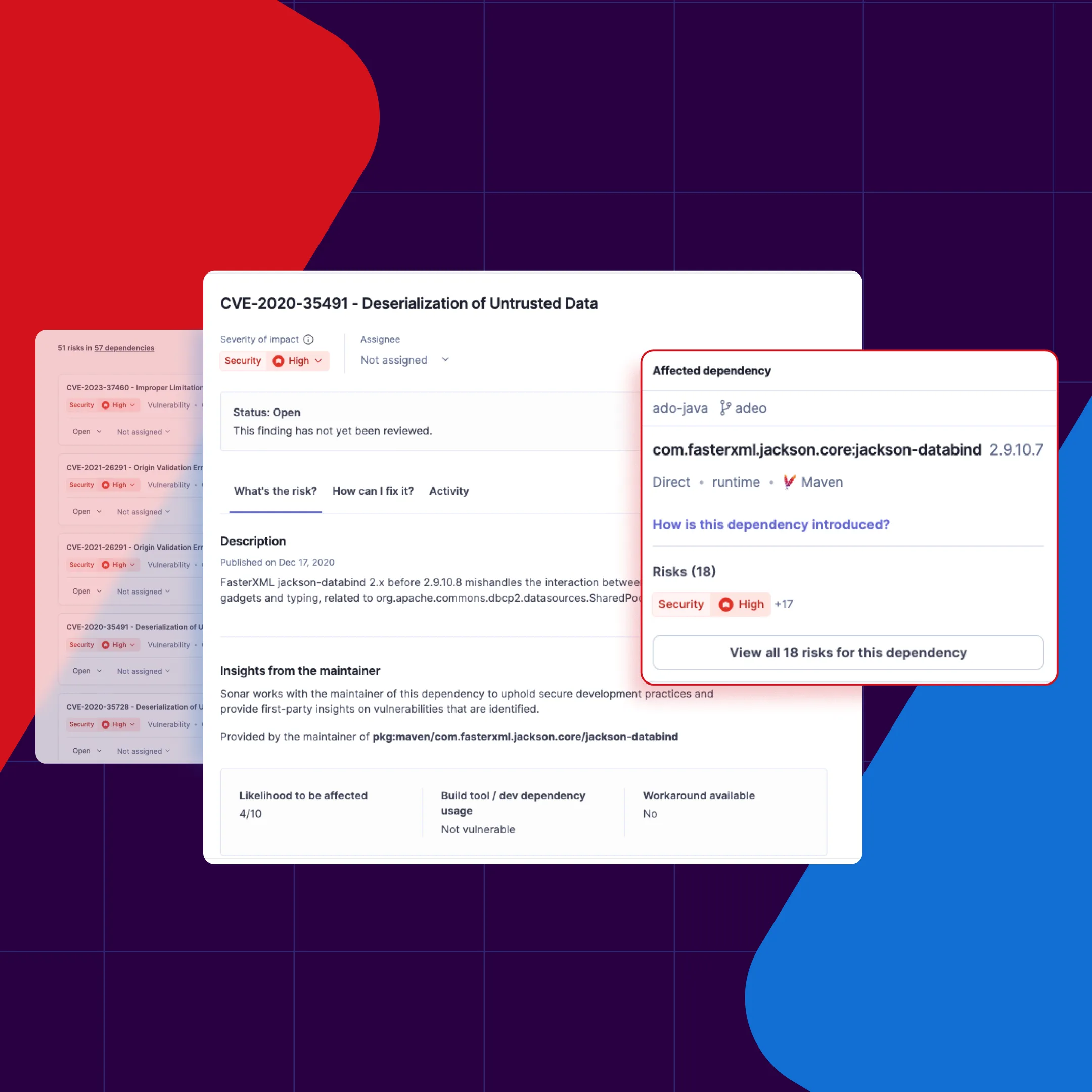
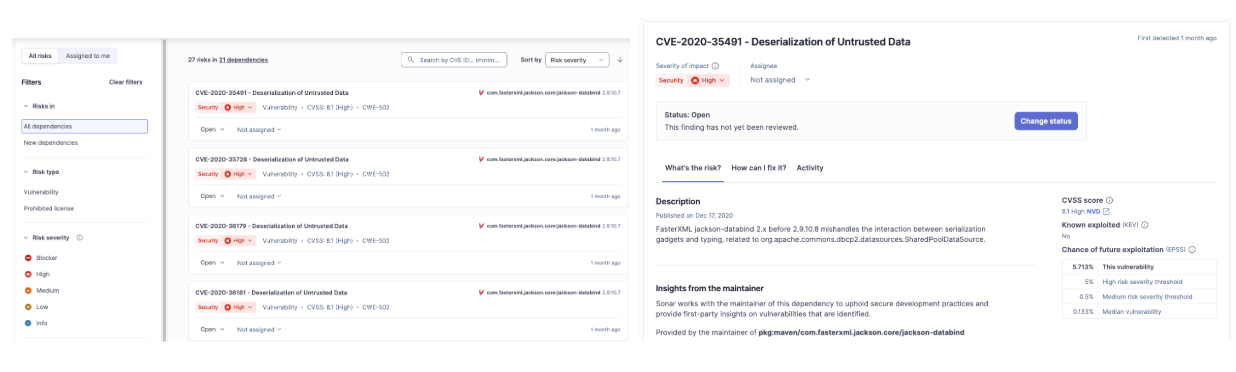
SonarQube Advanced Security provides deep visibility into your software supply chain through Software Composition Analysis (SCA). It analyzes your build configuration files (like pom.xml or build.gradle) and compares your dependencies against a comprehensive database of known vulnerabilities (CVEs).
Instead of requiring you to scour security bulletins, SonarQube integrated this check directly into your workflow. If a transitive dependency contains a critical flaw, the analysis flags it immediately and provides a clear path to remediation, often recommending the specific safe version to upgrade to.
Going deeper with advanced SAST
Standard SAST tools usually analyse your code to find security issues, but they only focus on your code. But what if you have an issue depending on how you use a 3rd party class and method?
SonarQube Advanced Security goes further by applying advanced static application security testing (SAST) to your dependencies. It uses taint analysis to trace the flow of data from your code into the library.
- The source: It identifies untrusted user input in your code.
- The flow: It watches that data as it passes into third-party libraries.
- The sink: It detects if that data reaches a dangerous function (like a SQL query or log entry) without being sanitized.
This reveals "invisible" vulnerabilities that traditional tools miss. You might write a controller that looks safe, but if it passes data to a library that handles it insecurely, you have a security gap. SonarQube exposes this interaction, allowing you to fix the root cause.
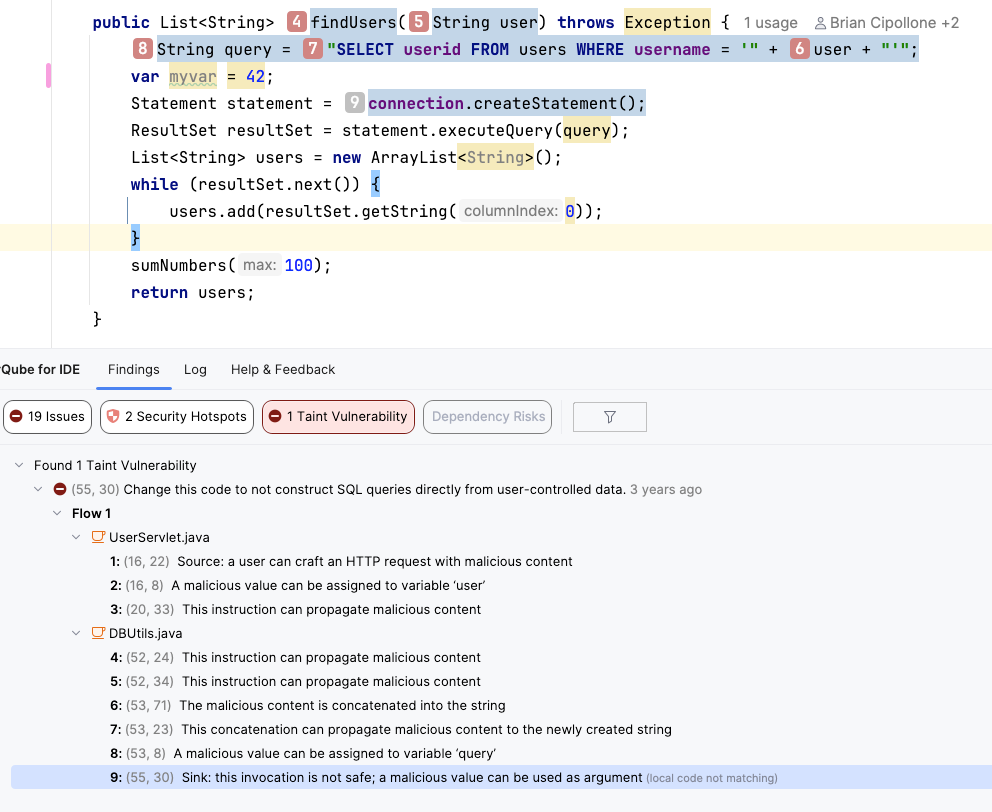
In this case it shows the different flow steps that result in a security issue because a value coming from the user is not transformed and passed to a 3rd party method that will use that value to query a database.
Managing license risk and compliance
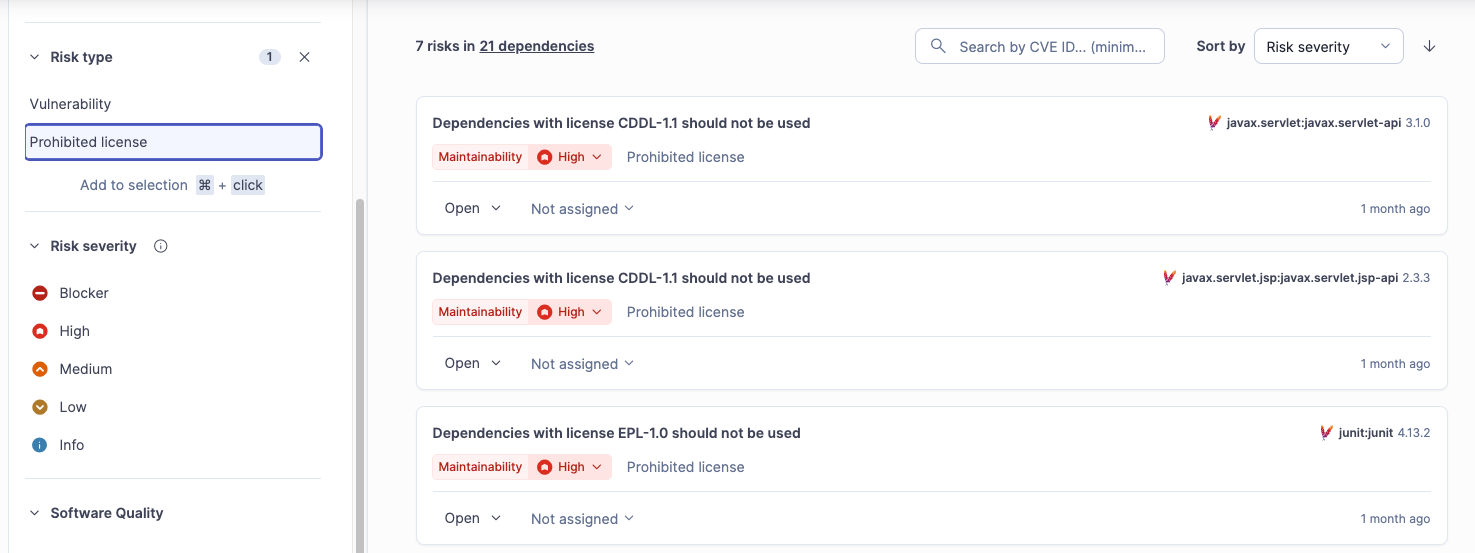
Security is not the only risk hiding in your pom.xml. Open source licenses vary widely, and some "viral" licenses (like GPL) can have significant legal implications for proprietary software.
SonarQube Advanced Security scans your dependencies to enforce license policies. It highlights libraries with risky licenses and allows organizations to approve or ban specific license types. This proactive check protects your intellectual property and prevents legal complications down the road.
Additionally, for industries with strict regulatory requirements, SonarQube automates the generation of a Software Bill of Materials (SBOM). This detailed inventory of every component in your software is essential for audits and compliance, turning a tedious manual task into an automated, downloadable asset.
Vibe, then verify
The use of third-party libraries and AI-generated code is essential for maintaining velocity. However, it requires a "trust and verify" approach. By integrating SonarQube Advanced Security into your development workflow, you ensure that every dependency—whether explicitly added or pulled in transitively—meets your standards for security and quality.
This allows developers to innovate with confidence, knowing that the "Trojan horses" in the supply chain will be caught long before they can cause harm.